shell
文件分析工具看一样,32位,无壳,然后就可以扔ida了
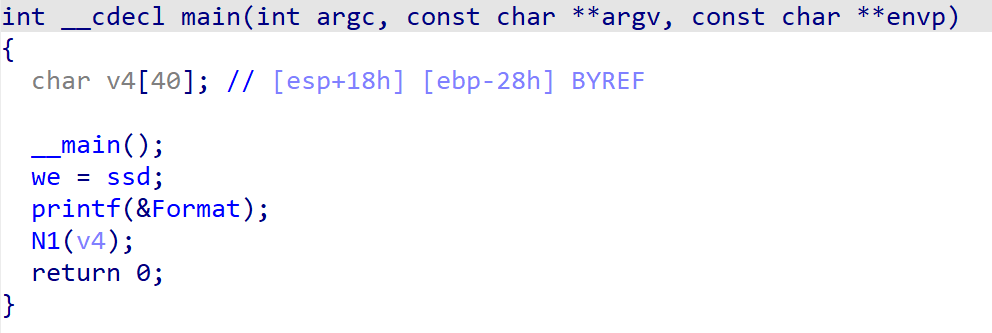
直接定位main函数,然后特殊的函数只有N1,进去看一下
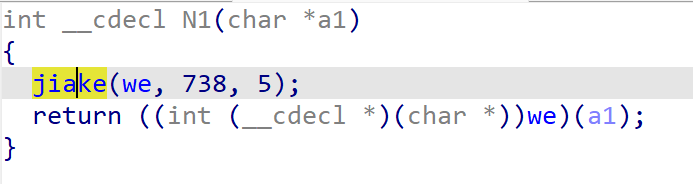
这个加密逻辑大概就是给代码解混淆了一下,在执行。去看一下他的解混淆逻辑
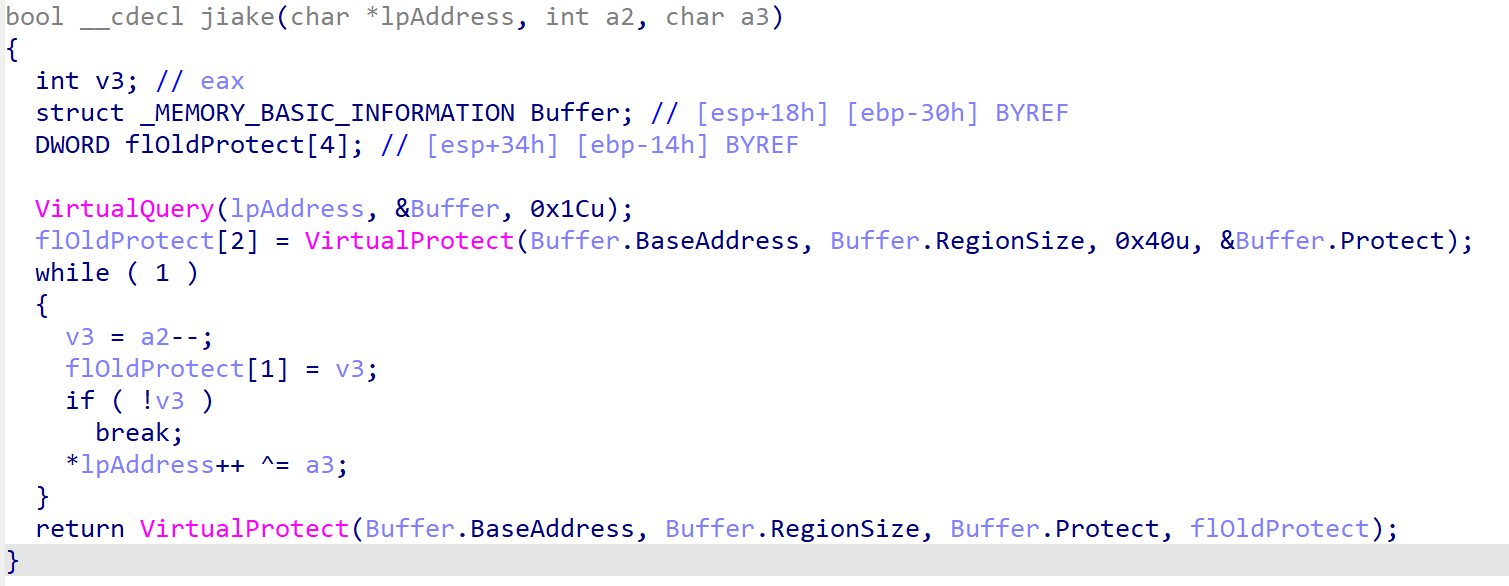
大致意思就是把ipaddress指向的代码段里每个字节异或5,去看一下ipaddress的初始值是从we传进来的,这是个全局变量,他的值是ssd,ssd是个函数名,到汇编窗口看一下他的地址,地址为0x401500。
接下来的事情就很好办了,两种方法,第一种是写ida python脚本,在ida中进行修改
import idc
addr = 0x401500
for i in range(738):
value = idc.get_wide_byte(addr) ^ 5
ida_bytes.patch_byte(addr,value)
print(hex(addr),hex(value))
addr += 1
print("finish")第二种是修改二进制文件,通过特征值在010中定位到ssd函数在文件中的地址,是0x900,然后再用python修改字节
# 作者(Author):Wankko Ree
# 链接(URL):https://wkr.moe/
# 来源(Source):Wankko Ree's Blog
with open('shell_e55a9fa7062b9e0b4ba412ca3584b543.exe', 'rb') as f:
data = bytearray(f.read())
for i in range(738):
data[0x900+i] ^= 5
data = bytes(data)
with open('shell_true.exe', 'wb') as f:
f.write(data)然后就看到了这个主要的加密函数ssd
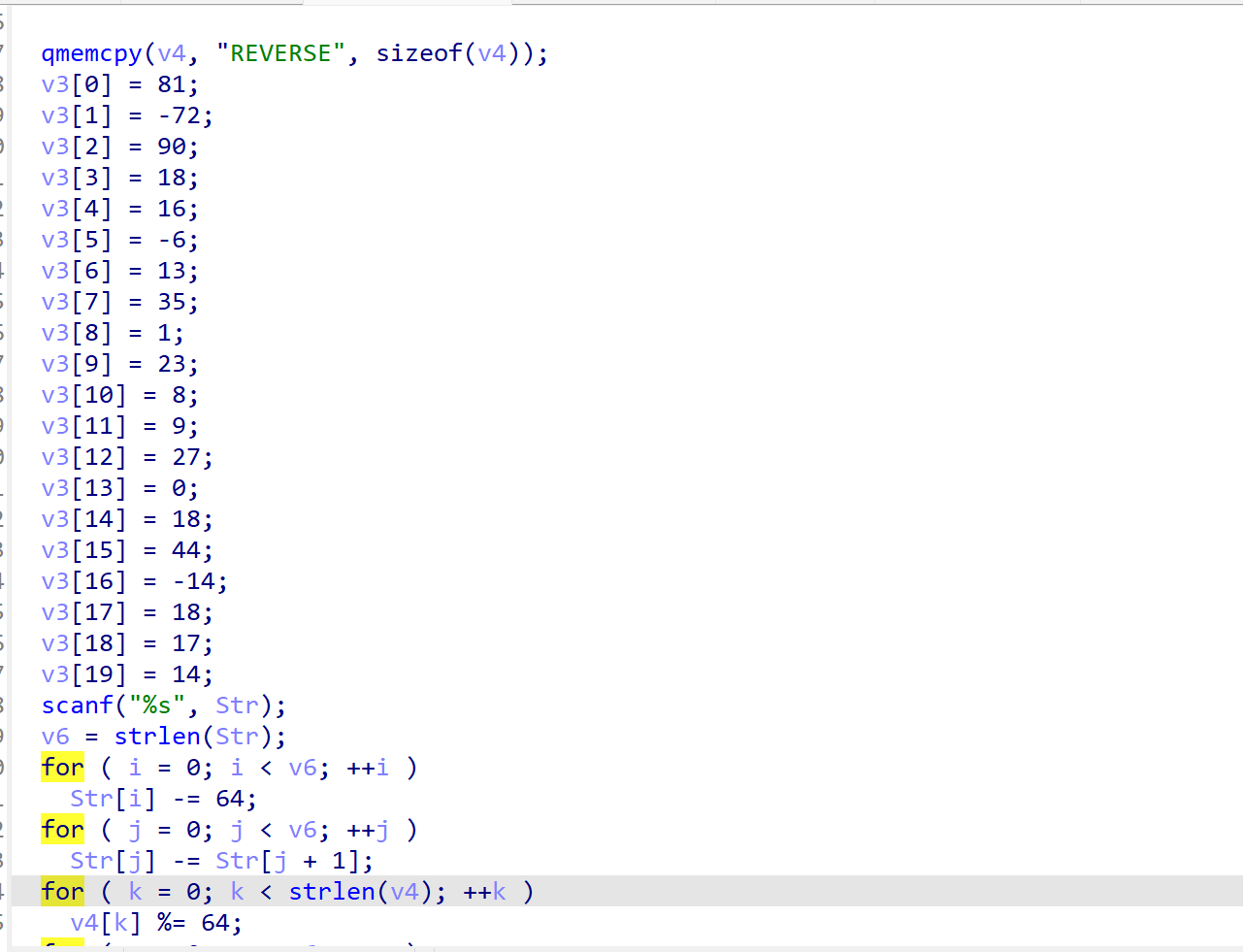
剩下的就是根据这几个简单的加密写出解密脚本了
python 版
# 作者(Author):Wankko Ree
# 链接(URL):https://wkr.moe/
# 来源(Source):Wankko Ree's Blog
target1 = [0x51,0xb8,0x5a,0x12,0x10,0xfa,0xd,0x23,1,0x17,8,9,0x1b,0,0x12,0x2c,0xf2,0x12,0x11,0xe]
target2 = bytearray("REVERSE".encode())
for i in range(7):
target2[i] %= 64
for i in range(20):
if target2[i % 7] & 1 != 0:
target1[i] -= 2
else:
target1[i] -= 1
for i in range(10):
tmp = target1[i]
target1[i] = target1[20 - i - 1]
target1[20 - i - 1] = tmp
for i in range(20):
target1[i] -= target2[i % 7]
print(target1)
for i in range(18, -1, -1):
target1[i] += target1[i+1]
target1[i] %= 256
for i in range(20):
target1[i] += 64
target1[i] %= 256
print(bytes(target1))c++版
#include<iostream>
#include<string>
using namespace std;
int main()
{
int cp[] = {0x51,0xb8,0x5a,0x12,0x10,0xfa,0xd,0x23,1,0x17,8,9,0x1b,0,0x12,0x2c,0xf2,0x12,0x11,0xe};
int key[] = {82,69,86,69,82,83,69};
for(int i = 0; i < 7; i ++)
{
key[i] %= 64;
}
for(int i = 0; i < 20; i ++)
{
if (key[i % 7] & 1 != 0)
cp[i] -= 2;
else
cp[i] -= 1;
}
int tmp = 0;
for(int i = 0; i < 10; i ++)
{
tmp = cp[i];
cp[i] = cp[20-i-1];
cp[20-i-1] = tmp;
}
for(int i = 0; i < 20; i ++)
{
cp[i] -= key[ i % 7];
}
for(int i = 18; i >= 0 ; i --)
{
cp[i] += cp[i+1];
cp[i] % 256;
}
for(int i = 0; i < 20 ; i ++)
{
cp[i] += 64;
cp[i] %= 256;
}
for(int i = 0; i < 20 ; i++)
cout << char(cp[i]);
return 0;
} 运行得到flag:flag{celebrate_you!}
